In the past few months, we have noticed a rise in spam emails that have an attachment of “.DOC” extension filename but actually is a “.MHT” file. This trending trick seems to be a new way to spread macro malware. A file with “.MHT” extension is a Web page archive format which saves images, text and objects from the original word document into a single file. You can convert a “.DOC” or a Word Document file into a “.MHT” or a single file Web page using Microsoft Word 2007. Here’s what the “.MHT” file extension looks like when opened in a text viewer. The encoded base64 ActiveMime data below is where the OLE file that has malicious macro script resides.
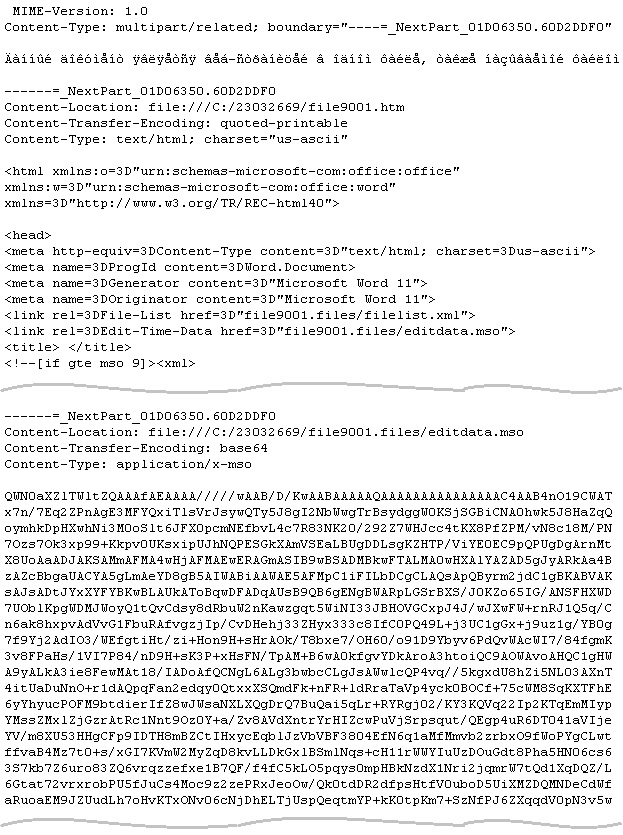
Dissection of base64 data of malicious “.MHT” file:
Decoding the base64 data above will have the ActiveMime data that looks like this:
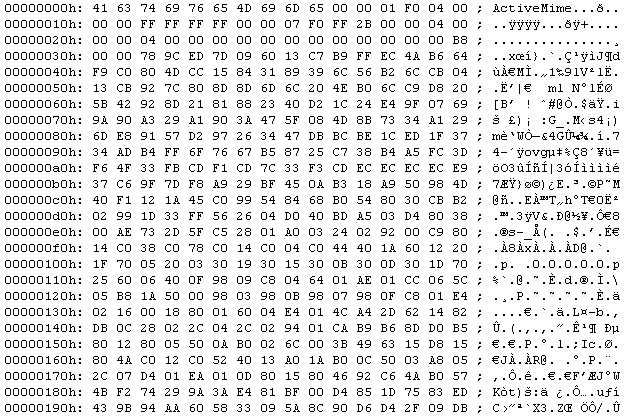
Now that we have the ActiveMime data that is ZLIB compressed. Decompressing this will lead us to the OLE file that has the malicious macro script.

So why does the author of this malware convert the “.DOC” file into an “.MHT” file and then rename the file extension to a “.DOC” file extension? I think thhe primary reason is to avoid being detected by antivirus products.
Here are screenshots of some of the spam emails:
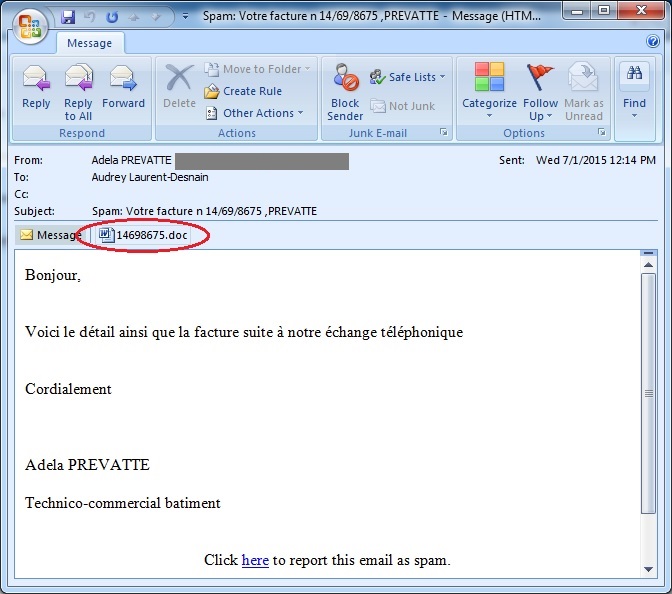
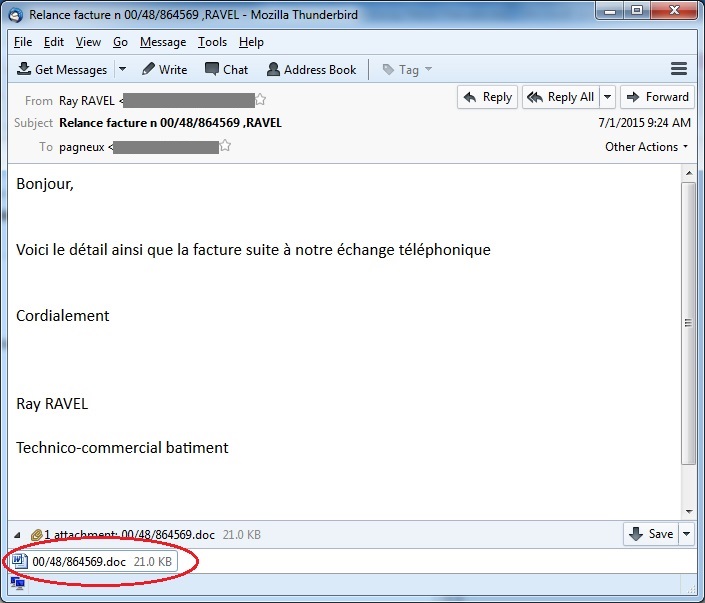
We detect the attachment file as W97M/Adnel or MHT/Dloader. This macro malware is usually attached in the spam emails as .doc files. It uses social engineering tricks to be able to run the malicious macro script that is disabled by default in Microsoft Office. Upon execution, it will download and execute other malware from a remote server.
CYREN highly recommends users to keep macros disabled and only enable it when opening trusted macro-enabled documents.
